Industrial environments demand security without disruption. At Evolvedge Technology Solutions, we specialize in Operational Technology (OT) cybersecurity designed specifically for industrial control systems (ICS), ensuring safety, availability, and compliance while enabling secure digital transformation. Our services align with IEC 62443, NIST SP 800-82, and industry best practices, delivered by engineers with real plant experience.
Secure Remote Access (SRA) for OT Environments
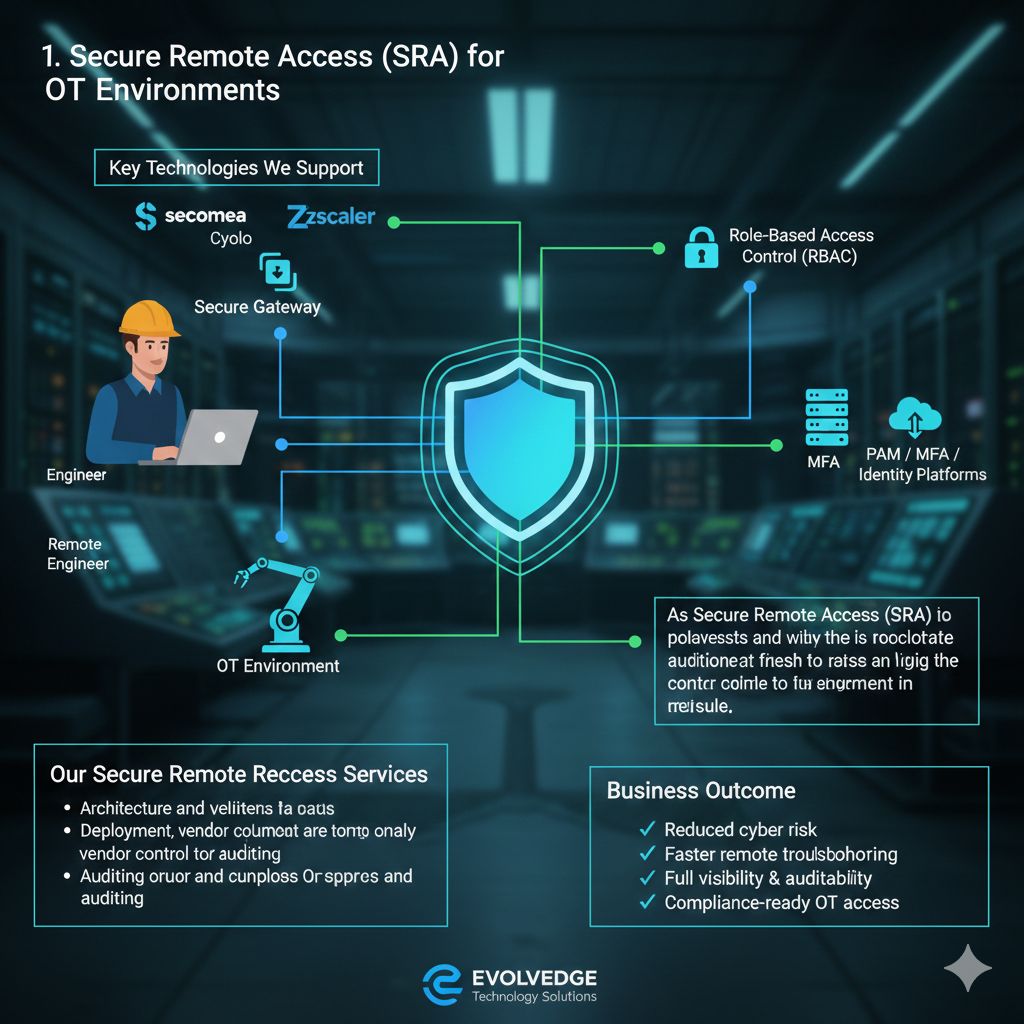
Remote access is essential for modern industrial operations – but unmanaged access is one of the biggest OT cyber risks. We design, deploy, and audit secure, vendor-approved remote access architectures that protect OT networks without impacting production.
Key Technologies We Support
- Secomea Secure Remote Access
- Cyolo Privileged Access for OT
- Zscaler Privileged Remote Access (PRA)
- Integration with PAM, MFA, and identity platforms
Our Secure Remote Access Services
- OT Remote Access Architecture Design
- Secure access design for brownfield & greenfield plants
- IT/OT network segregation with DMZ-based access
- Jump-host and broker-based access models
- Zero Trust–aligned OT access architecture
Deployment & Configuration
- Secure gateway and access broker setup
- Role-based access control (RBAC) for vendors & engineers
- Multi-factor authentication (MFA) enforcement
- Session recording and command auditing
Vendor & Third-Party Access Control
- Controlled OEM and integrator access
- Time-bound and approval-based sessions
- Least-privilege enforcement
- Compliance with IEC 62443-3-3 SR 1.1 & SR 1.2
Secure Remote Access Audit & Hardening
- Review of existing Secomea / Cyolo / Zscaler setups
- Misconfiguration and exposure analysis
- Policy hardening & access optimization
- Compliance gap mapping
Business Outcome
✔ Reduced cyber risk
✔ Faster remote troubleshooting
✔ Full visibility & auditability
✔ Compliance-ready OT access
OT Intrusion Detection & Network Visibility (IDS)
Traditional IT security tools do not work in OT networks. We deploy passive, non-intrusive OT IDS solutions to provide real-time visibility without disrupting operations.

Supported OT IDS Platforms
✔ Nozomi Networks
✔ Claroty
✔ Armis
✔ Integration with SIEM / SOC platforms
Our OT IDS Services
- Passive discovery of PLCs, RTUs, HMIs, DCS
- Identification of firmware versions & protocols
- Network communication mapping
- Shadow asset detection
- Detection of unauthorized devices
- Malicious traffic & lateral movement detection
- Protocol misuse and abnormal behavior alerts
- Known ICS malware indicators
- Normal traffic behavior baselining
- Process-aware anomaly detection
- Alert tuning to reduce false positives
Business Outcome
OT Cybersecurity Risk Assessment (IEC 62443)
We perform structured OT cybersecurity risk assessments aligned with IEC 62443, focusing on real-world plant risks rather than checkbox compliance.

Our IEC 62443-Based Assessment Approach
Scope Definition & Asset Identification
✔ Zone & conduit identification
✔ Critical asset classification
✔ Process safety impact analysis
✔ OT system inventory
Threat & Vulnerability Analysis
✔ Threat modeling for OT environments
✔ Identification of insecure protocols & architectures
✔ Remote access and vendor access risk review
✔ IDS & monitoring maturity assessment
Risk Evaluation
✔ Likelihood vs impact analysis
✔ Safety, availability, and compliance risk scoring
✔ Mapping to IEC 62443 Security Levels (SL1–SL4)
Gap Analysis Against IEC 62443
✔ IEC 62443-2-1 (Policies & governance)
✔ IEC 62443-3-3 (System security requirements)
✔ IEC 62443-4-2 (Component security)
Remediation Roadmap
✔ Prioritized risk treatment plan
✔ Technology, process & people recommendations
✔ Quick wins vs long-term improvements
✔ Budget-aligned security roadmap
Deliverables
✔ OT Risk Assessment Report
✔ IEC 62443 Compliance Gap Matrix
✔ Zone & Conduit Diagrams
✔ Executive & Technical Summary
✔ Actionable Improvement Roadmap
OT Network Segmentation & Zero Trust
We design OT-specific segmentation strategies to limit blast radius and prevent lateral movement.
✔ Purdue model–aligned segmentation
✔ VLAN, firewall, and conduit-based isolation
✔ Zero Trust principles for OT
✔ Integration with IDS and secure remote access
OT Security Governance & Program Development
✔ OT cybersecurity policy development
✔ OT incident response planning
✔ Vendor cybersecurity requirements
✔ OT security awareness & training
Why Evolvedge Technology Solutions?
Industries We Serve
Ready to Secure Your OT Environment?
Whether you are starting your OT security journey or enhancing existing controls, we help you secure operations without disrupting production.
📩 Contact us to discuss your OT cybersecurity requirements.
